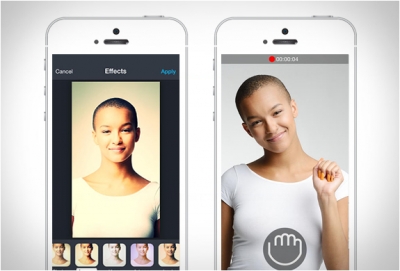
What is special in Speaking Photo app?

Turn your pictures into stories with Speaking Photo, an app that lets you add sound to any photo. It allows you to tell a story along with the image before you share it on Facebook, YouTube or via email. The storyboard feature gives users a chance to select multiple photo/audio pairs and customize their play order, creating a larger movie to share. Available for iOS and Android.
With SpeakPic, the voice of the translator will be really fun for you and friends.
Have you thought about making your friend sing his/her team's anthem? Or maybe an unexpected declaration of love. With SpeakPic, anything is possible.
You can change the voice with different effects to make the end result even funnier.
There are dozens of voices to choose from, in multiple languages.
Picture Credit : Google